Security is mostly a superstition. If there is a beautiful thing out there, human won’t leave it. They just try to sneak in and see what’s cooking inside. Okay, I’ll stop my story on security. A critical iOS vulnerability that Apple patched on Friday gives attackers an easy way to clandestinely circumvent the most widely used technology for preventing eavesdropping on the Internet. Now, there’s strong evidence that the same flaw also exposes sensitive e-mail and Web communications on fully patched versions of OS X, with no indication that there is a patch currently available for the millions of people who use the Mac operating system.
The vulnerability has been confirmed in iOS versions 6.1.5, 7.0.4, and 7.0.5, and OS X 10.9.0 and 10.9.1. Readers should immediately update their iPhones and iPads to versions 7.0.6 or 6.1.6, preferably using a non-public network. And people using Macs should avoid public network for the time being.
According to researchers, the flaw causes most iOS and Mac applications to skip a crucial verification check that’s supposed to happen when many transport layer security (TLS) and secure sockets layer (SSL) connections are being negotiated. Specifically, affected apps fail to check that the fugacious public key presented by servers offering Diffie Hellman-supported encryption is actually signed by the site’s private key. Attackers with the ability to monitor the connection between the end-user and the server can exploit this failure to completely decrypt and manipulate the traffic by presenting the app with a forge key.
An attacker “can basically set up a connection and pretend to be Google.com,” Matt Green, a Johns Hopkins University professor specializing in encryption, told Ars. The attacker “can basically say: ‘Hey, I’m Google, here’s my signature. And since nobody is actually going to check the signature, the attacker just puts nonsense in there.”
“This sort of subtle bug deep in the code is a nightmare,” Langley, who is also a Google employee, wrote. “I believe that it’s just a mistake and I feel very bad for whomever might have slipped in an editor and created it.”
An online tech report says. In addition to this flaw could impact HIPAA.
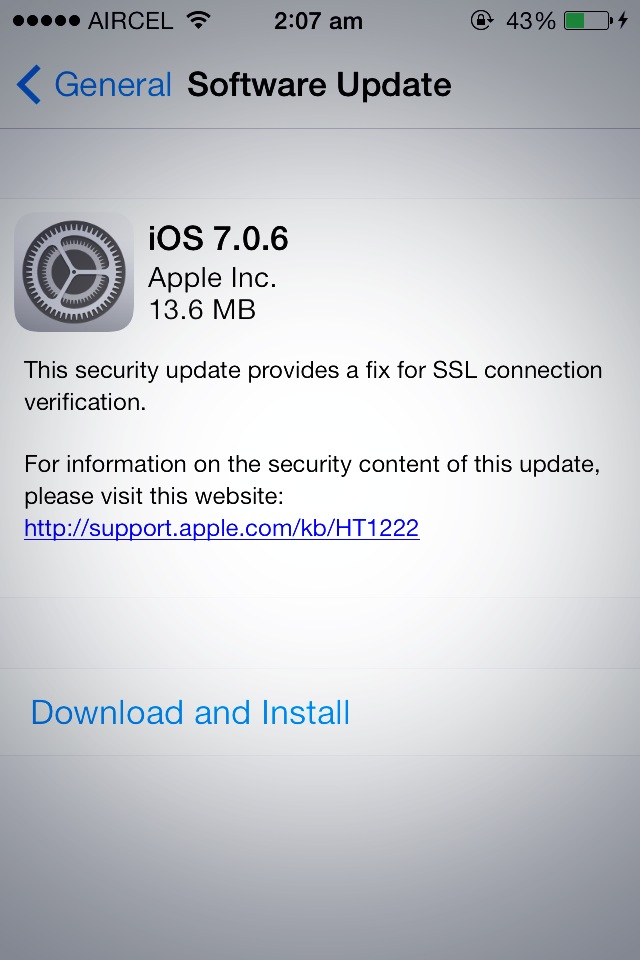
Apple rarely comments on matters involving security, particularly those involving vulnerabilities that remain unpatched. But they responded liberally about the issue. Security content of iOS 7.0.6
iOS 7.0.6
- Data Security
Available for: Apple iPhone 4 and later, iPod touch (5th generation), iPad 2 and later
Impact: An attacker with a privileged network position may capture or modify data in sessions protected by SSL/TLS
Description: Secure Transport failed to validate the authenticity of the connection. This issue was addressed by restoring missing validation steps.
CVE-ID
CVE-2014-1266